Long ago, I configured my iMC server to use AD based operator login. you can read the post here. After having ClearPass up and running I will do the iMC operator login with radius. This post describes how this works.
iMC Operator Login: Prepare ClearPass
The first step is to prepare ClearPass. Those are the normal steps to do radius authentication with ClearPass. First, add iMC to the device list. Login to the policy manager part of ClearPass and go to “Configuration–>Network–>Devices” and add a new Device:
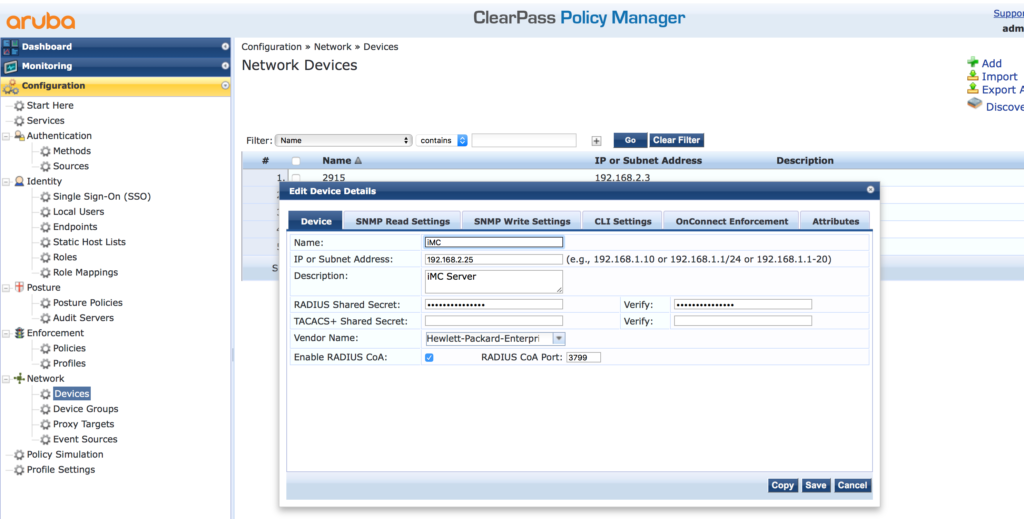
You can also add iMC to an existing device group and create one for iMC. Go to “Configuration–>Network–>Device Groups”:
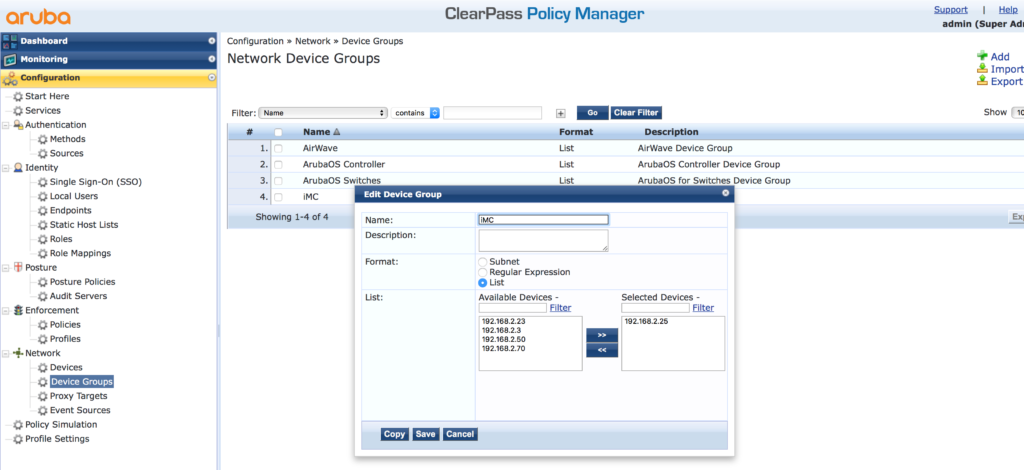
After iMC is in the list of allowed devices, ClearPass needs a service to handle the requests. But before creating the service itself, create all the needed components. Start with the enforcement profile. Go to “Configuration–>Enforcement–>Profiles” and add a new profile:
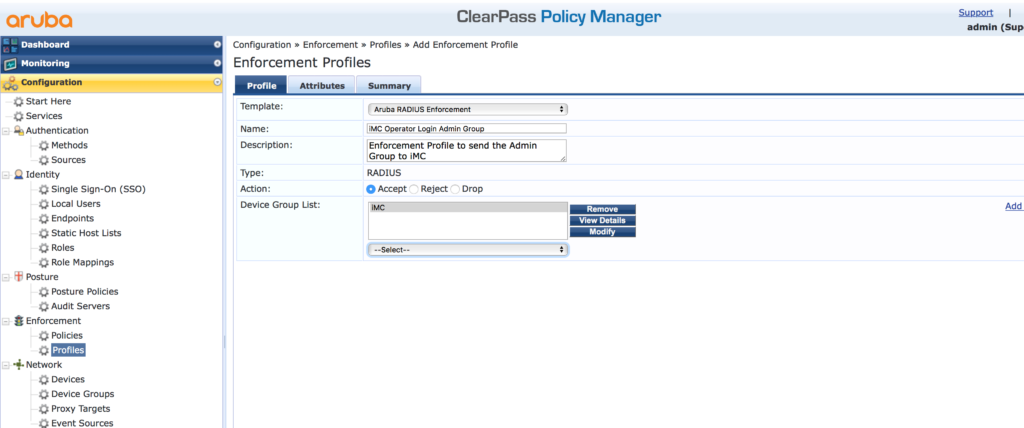
Select the “Aruba Radius Enforcement” template and assign a name and a description. If you created a device group for iMC add this group to the “Device Group List”. Click “Next”:
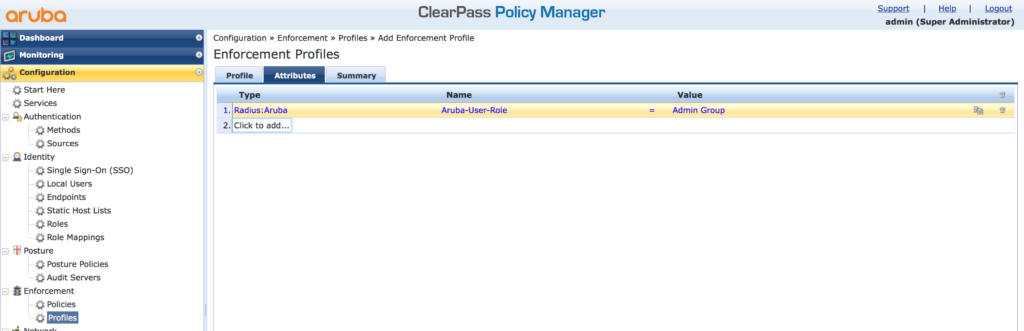
On the “Attributes” tab, stay with the “Radius:Aruba” “Type” and the “Aruba-User-Role” “Name”. I use the “Admin Group” “Value”. You can choose whatever you need and is applicable to your environment. Consider, that the value of this field, is used to assign the group to the iMC operator, later in iMC. My recommendation is, to use the same name, as the operator group name in iMC. Afterward, click “Next” to get the summary or “Save” to finish the wizard. Add as many profiles as needed. Should be the same number of profiles, as operator groups in iMC.
Now, create the “Enforcement Policy” to create rules to decide, which profile should be used for a specific operator. I use the membership of an AD group. Here is how. Go to “Configuration–>Enforcement–>Policies” and create a new “Policy”:
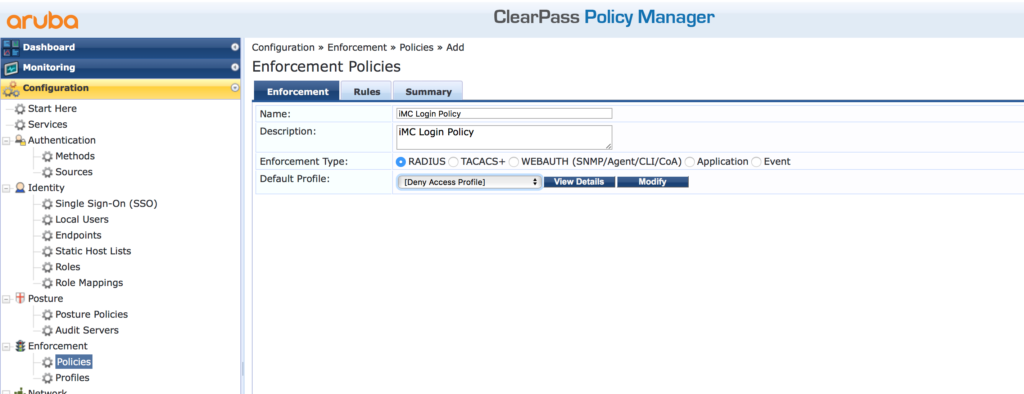
Assign a “Name” and a “Description” to the new “Policy” and select the “RADIUS” “Enforcement Type”. I always us the “[Deny Access Policy]” as the “Default Profile” to make sure that all requests, not matching the rules get a deny. Click “Next” to get to the “Rules” screen and add a new rule:
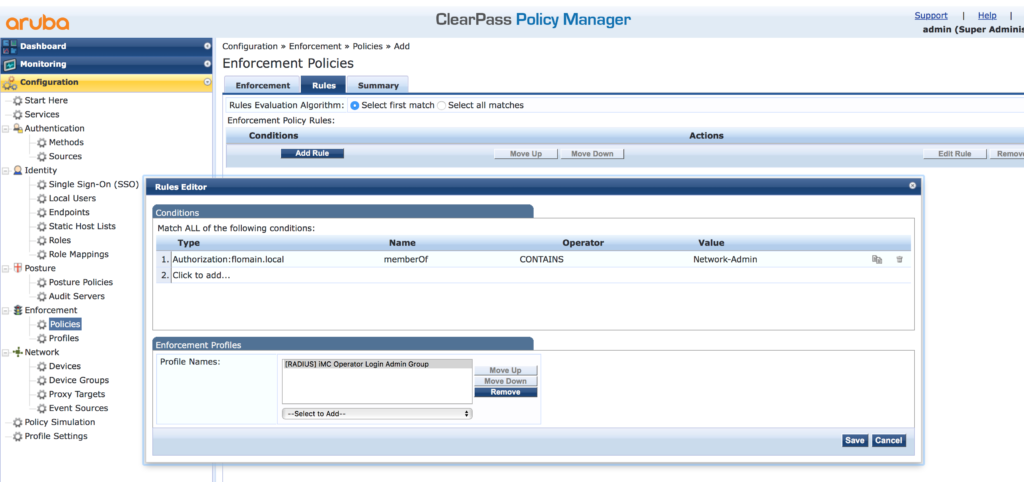
I use my AD for the “Type” and the “memberOf” “Name”. The “Operator” is “CONTAINS”. The “Value” is the name of the group in my AD. If this rule has a match, the created profile is used in the response. Save the rule. You should create rules for every profile you have created. Afterward, save the policy with the click of the “Save” button.
The last and final step is to create the service. Go to “Configuration–>Services” and create a new service:
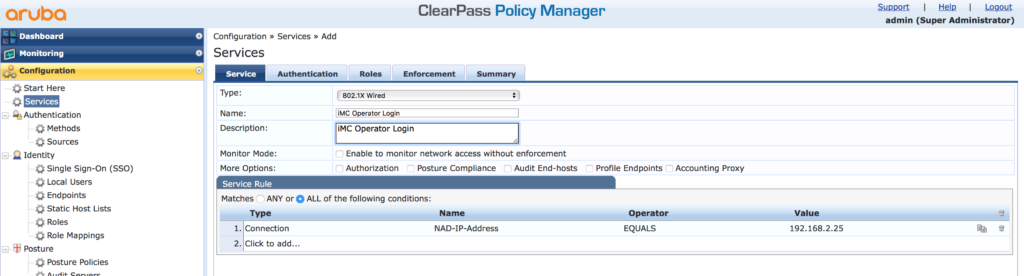
Select the “802.1X Wired” “Type” and assign a “Name ” and a “Description”. Delete all existing rules. From my point of view, the request can only be identified by the IP address of iMC. Therefore I use the IP as the rules to select this service.
Click “Next to get the next screen:
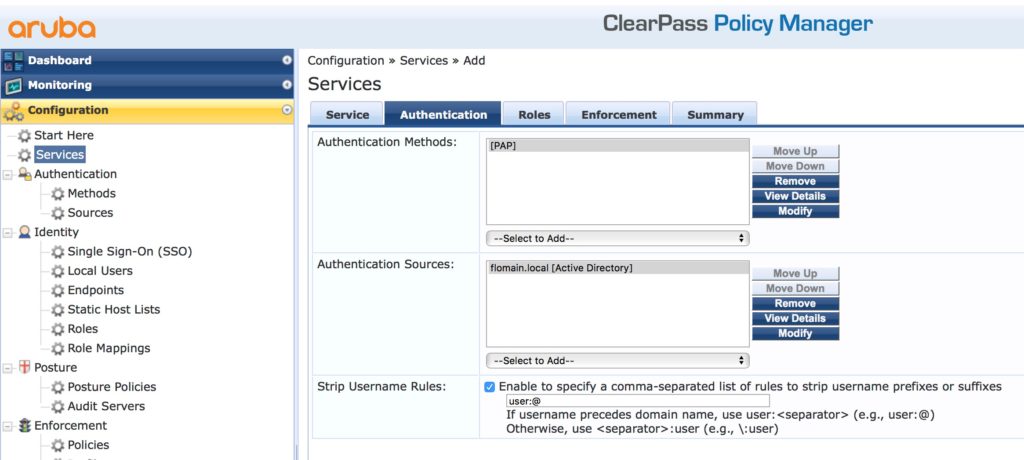
Select the “Authentication Source”. In my case, it is my AD. The combination, AD and iMC allows only the “[PAP]” “Authentication Method”. I also strip the “@flomain.local” prefix from the username with the “Strip Username Rules”. Click “Next” until you reached the “Enforcement” tab:
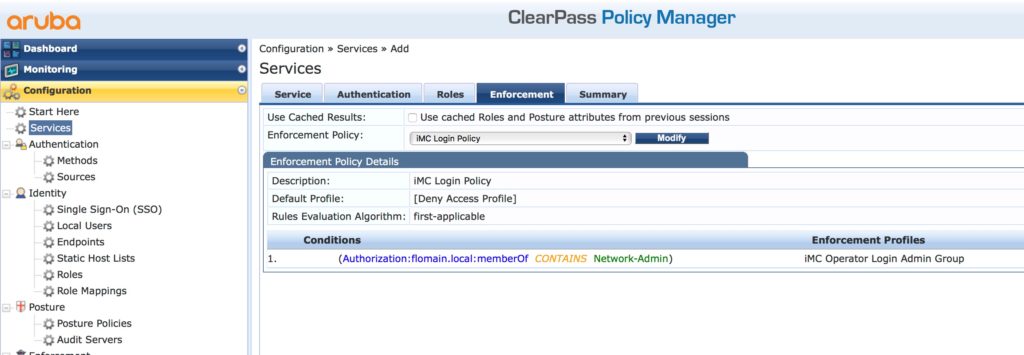
Select the “Enforcement Policy” you have created earlier. Click “Save” and you are done for the ClearPass part.
iMC Operator Login: iMC Configuration
The last part is to configure iMC to use ClearPass for authentication. To configure radius authentication for iMC, login to iMC and go to “System–>Operator Management–>Authentication Server” and configure the “Radius Server”:
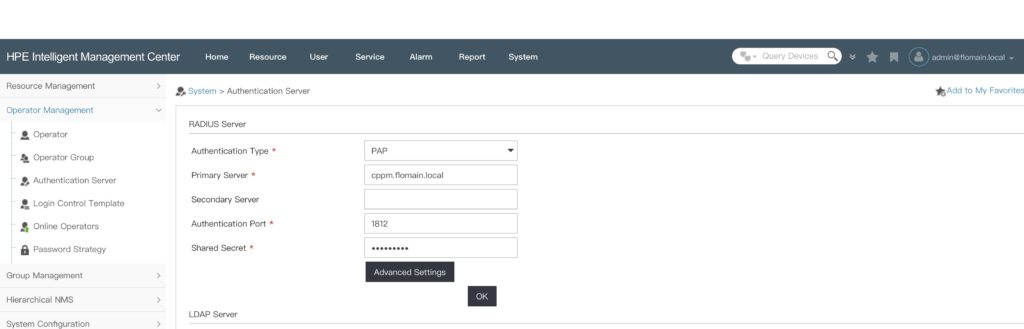
Make sure, to use the same “Shared Secret” as you configured in ClearPass. Click the “Ok” button to save the settings. Afterward, you can create new iMC operators which are using radius for the authentication.
To avoid this extra step of creating users manually, click the “Advanced Settings” button:
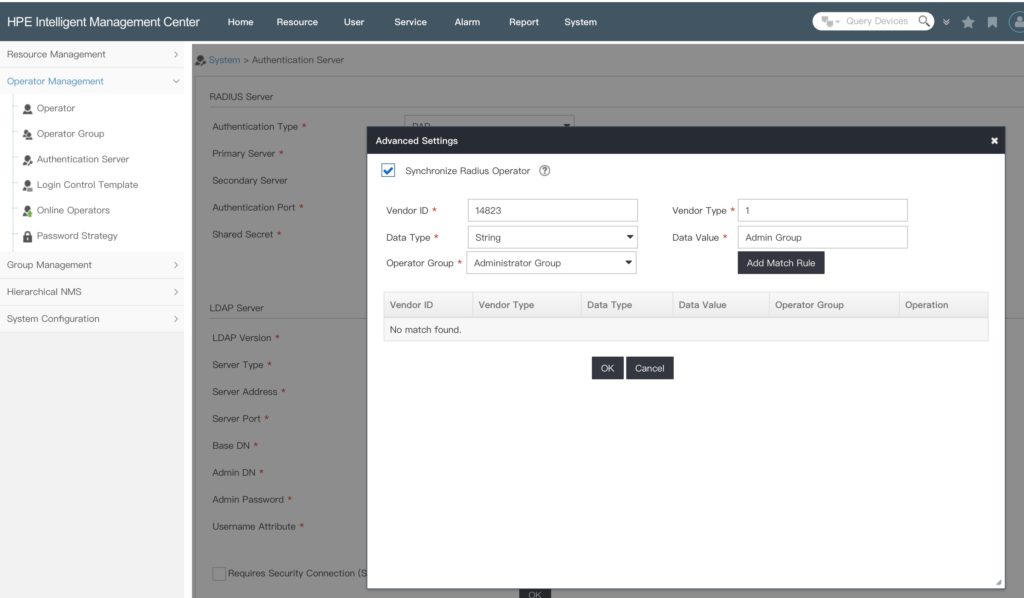
Check the “Synchronize Radius Operator” checkbox and create a matching rule. For ClearPass with the configuration above, you can use the settings in the picture. Just replace the “Data Value” with the value you return in your “Enforcement Profiles”. Create a “Match Rule” for every “Enforcement Profile” you have created. At the end, click the “Ok” button to save the settings.
If a new operator authenticates to iMC and ClearPass returns a “Data Value” which can match, the operator is created by iMC and get the access rights from the corresponding operator group.
If you use a different radius server, you can get the “Vendor ID” and “Vendor Type” information from Wireshark:
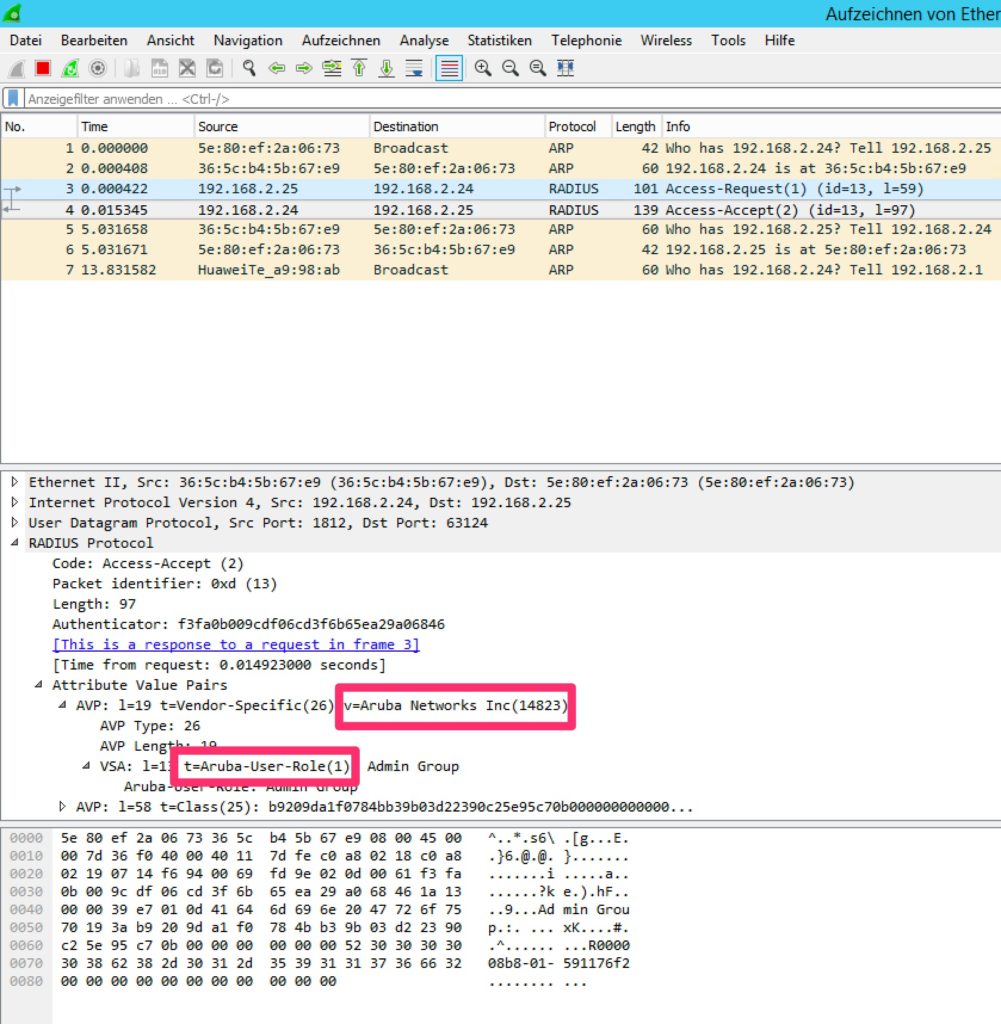
From the trace above, you can see the values. Those values can be extracted from traces with different radius server as well. This makes the solution with iMC so flexible.
What is your preferred radius server? And why? Send me your answer as a comment below. Feedback and questions are welcome as well.
Hello,
first thank you for you work it really help, i have problem, I done as you done above but not working it give me error:
((Authentication server is not available. Please contact the administrator.))
can you help ?
Hi Mohammad,
Do you see the authentication request at the radius server? Does the radius server send a response?
BR
Florian
Hi Florian,
yes after some days I notice the authentication request, the problem was the request come from server IP of IMC not the Virtual IP of IMC I use before the IP for HM that why not working,
now I’m working to connect ClearPass with Palo Alto using TACACS+ but no luck ;(
thank you for your help.
Hi Mohammad,
thanks for sharing the solution.
Many thanks,
Florian