As described in earlier posts I run EVE-NG in Azure. For several reasons, I need a direct connection to EVE-NG and the nodes within EVE-NG. I could use an Aruba Gateway in Azure but this would consume too much of my tight budget, so I decided to use an Azure Site to Site VPN with my Gateway at home.
The setup of the Azure Site to Site VPN was a little bit tricky, so I decided to create this post and share my findings.
Build the Azure Site to Site Gateway
Let’s start with the Azure part first. This is just a simple click through the GUI part. I use the cheapest version of the Azure Gateway to save as much money as possible so I go with the Basic VPN Gateway. I assume, that you have some basic knowledge of Azure and will not describe every detail. This would go above the scope of this post.
Create a new VNET, if you do not have already one. It could be a very simple VNET, just make sure your “Address Space” did not overlap with your local one. From that VNET create a new subnet, dedicated to the gateway. No other devices can be part of this subnet. I have two subnets in my VNET, one for the gateway and one for my EVE-NG:
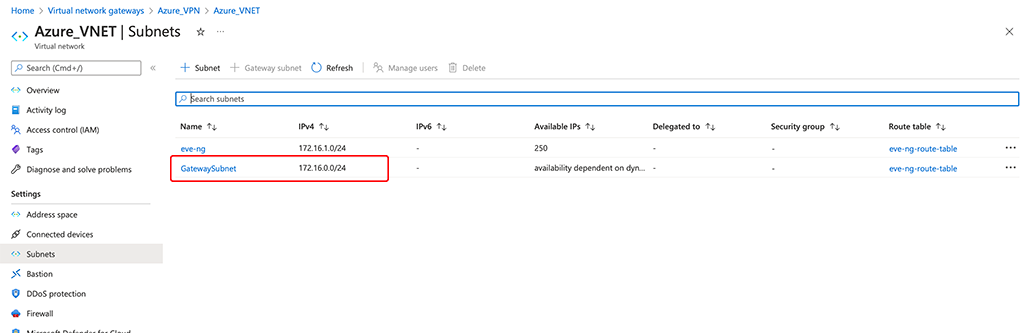
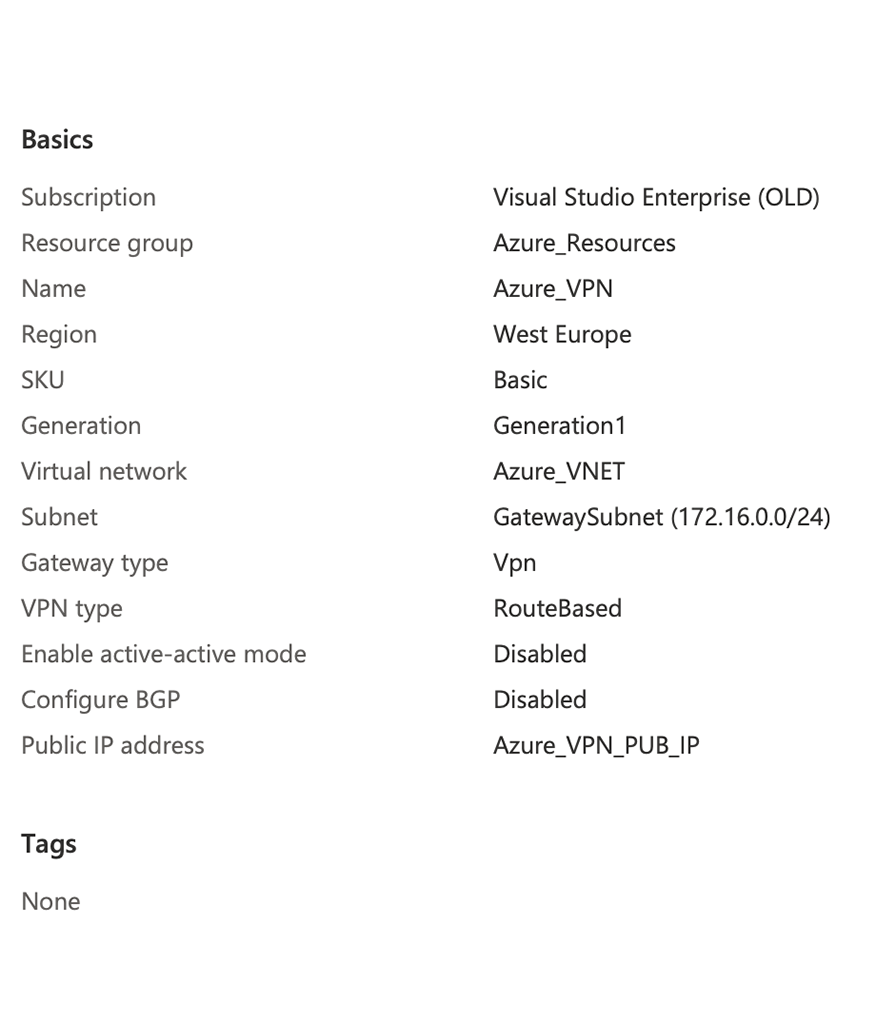
Next, create a Basic Azure VPN using the VNET and subnet above. Also, create a new public IP, or use an existing one. This would be the IP you connect the Aruba Gateway to. “Gateway type” is VPN and “VPN type” is “Route-based”. You do not need BGB for this simple setup:
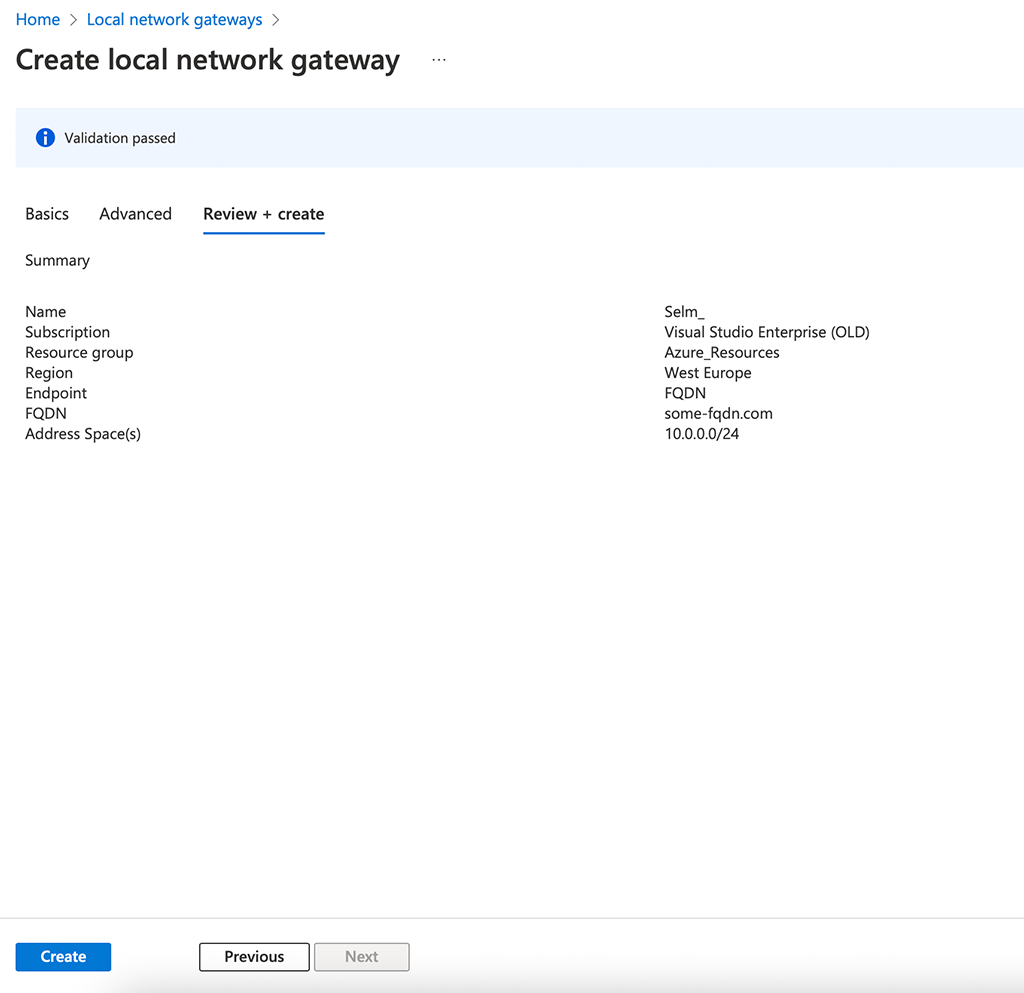
Now, create the “Local network gateway”. This represents the Aruba Gateway including the networks behind the gateway. This is somehow static routing as we do not use BGP:
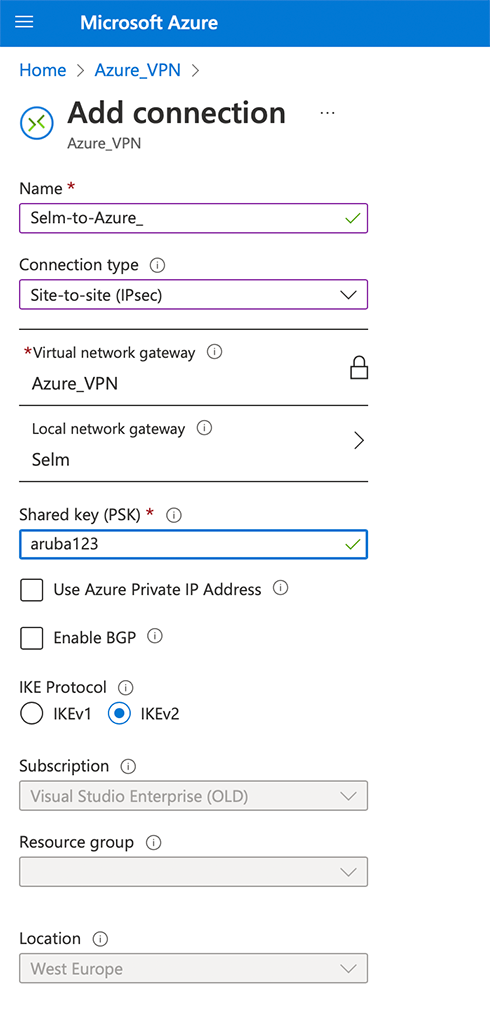
Now, go back to your “Virtual network gateway” and create a new connection like the one below. Select your “Local gateway” from above and create a “Shared key”:
Afterward, select your connection and make sure you have the following “Configuration”:
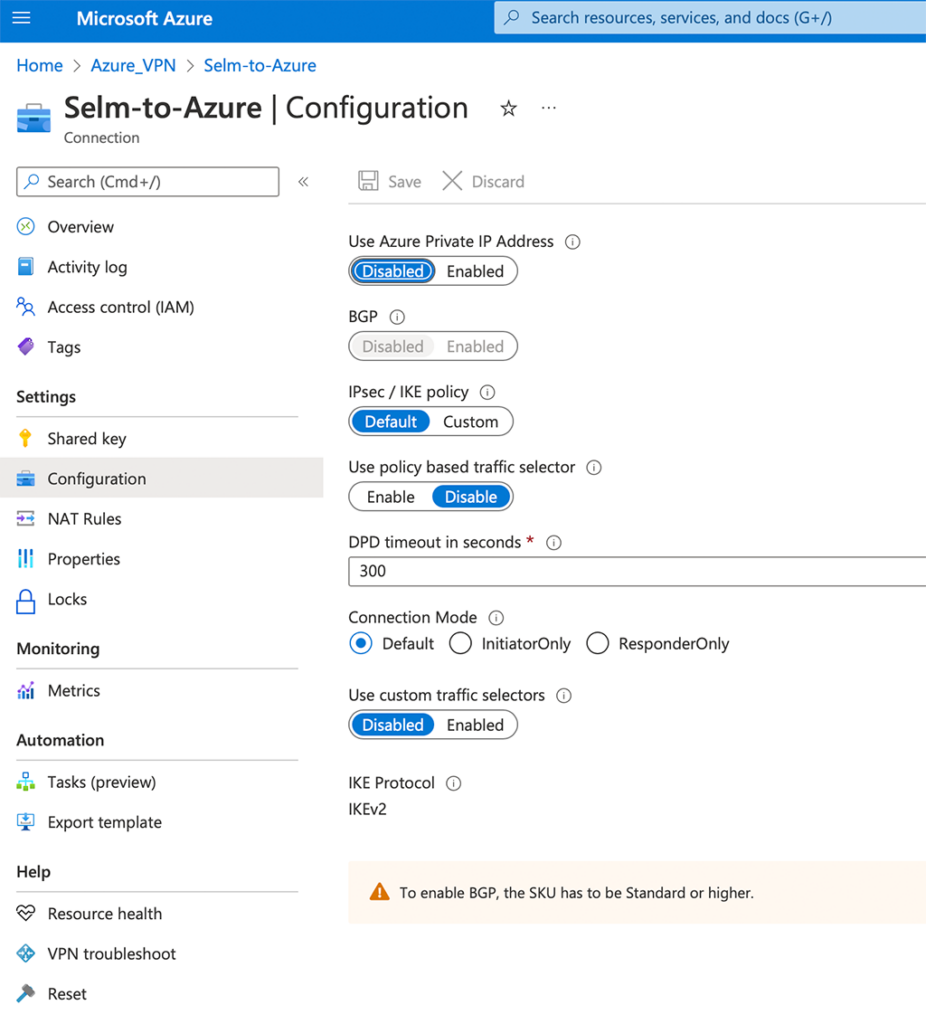
That’s all you need to do for the Azure part, let’s head over to Aruba Central and configure the Aruba Gateway.
Build the Aruba Gateway Site to Site VPN
I use Aruba Central to configure my Gateway for the Site to Site VPN. As a Mobility Controller is using the same underlying OS you can do the same there. The config should be quite similar.
The first step is to adjust the DPD timing for IPSec. In Aruba Central select the group with the Gateway and go to “Devices–>Gateway–>Config–>VPN–>DPD” and adjust the settings as below:
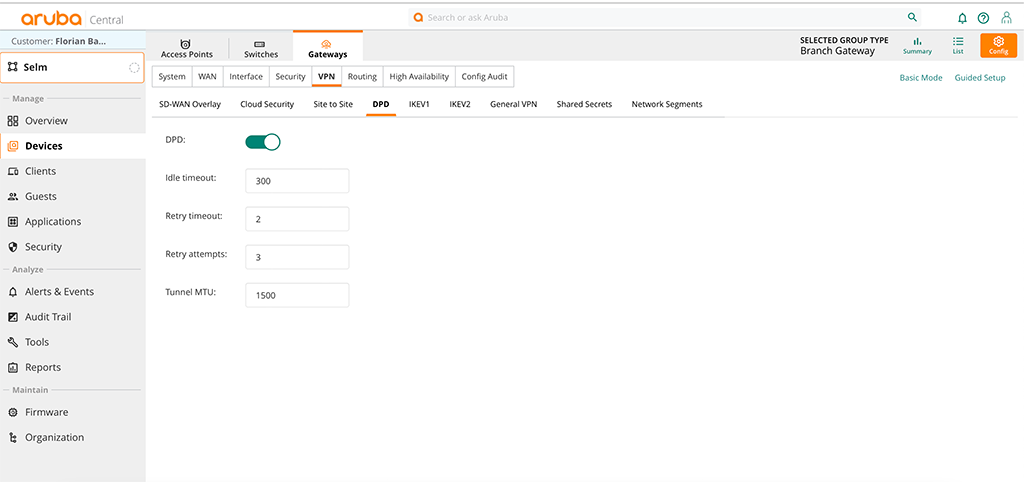
Adjust the “Tunnel MTU” to your needs.
Now go to “Devices–>Gateways–>Config–>VPN–>Site to Site” and create a new “IPSec maps”:
First, go to “Transforms” and create a new transform with the settings below:
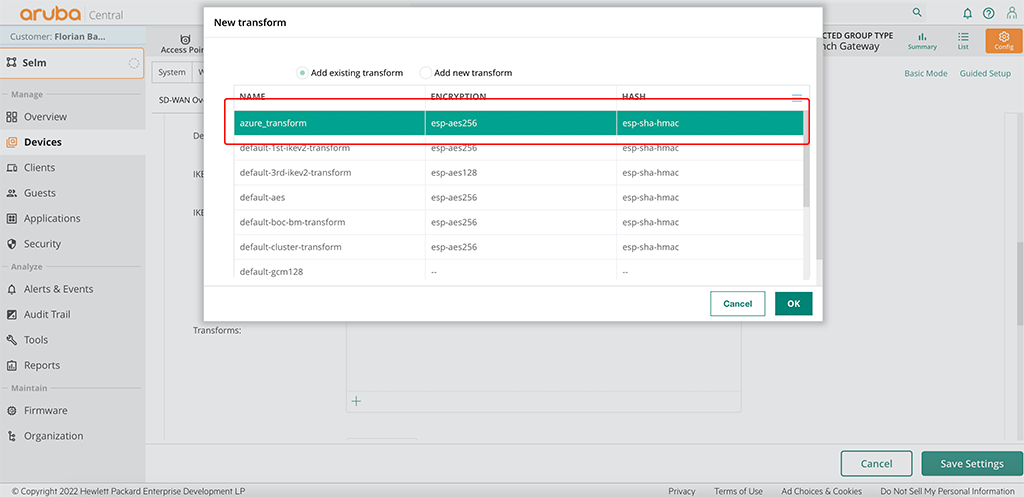
This is to match the settings in Azure. Also, add a second “Transform” to the table. I use “default-3rd-ikev2-transform”. Without a second transform, it will not work. Even if they always chose the first one, which we created above.
Now get back to the top of the form and enter the required information:
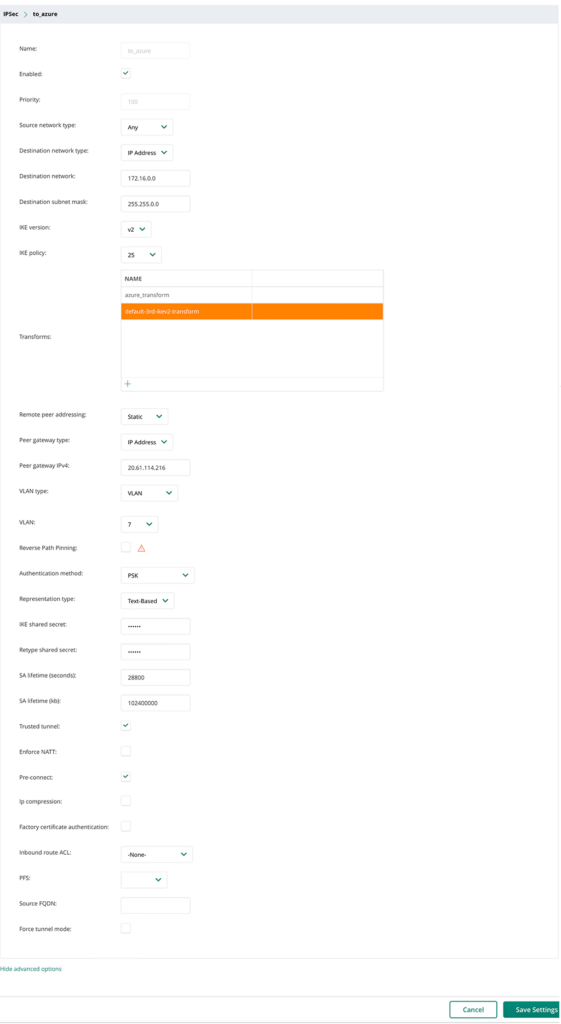
Replace the “Name” with your name for the IPSec map. Also, replace the “Destination network” to align with your VNET in Azure. “Peer gateway IPv4” is your public IP in Azure for the Virtual Network Gateway. “Pre-Connect” is an important point. Check this one to keep the tunnel connected. Without the checkmark, the tunnel is built only if required.
“Save Settings” to finally create the config. You can now check if the tunnel is up. Either in Aruba Central:
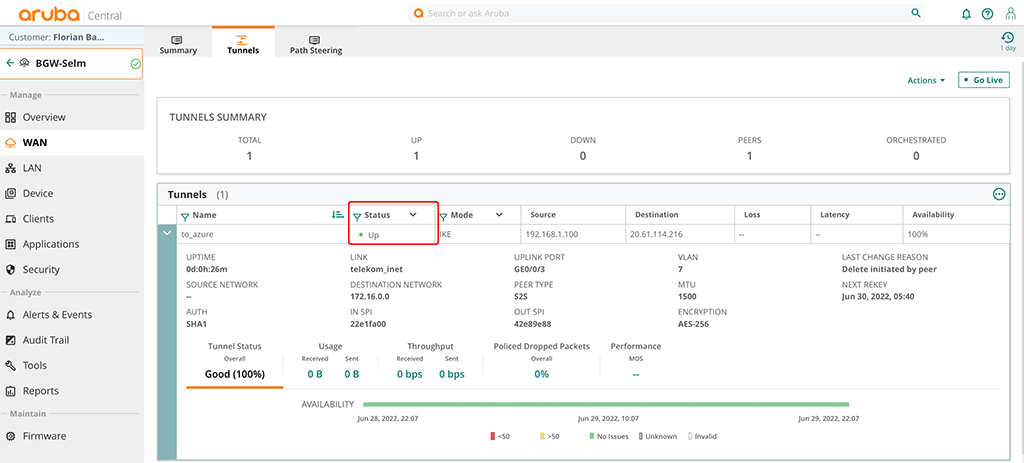
Or within Azure as well:
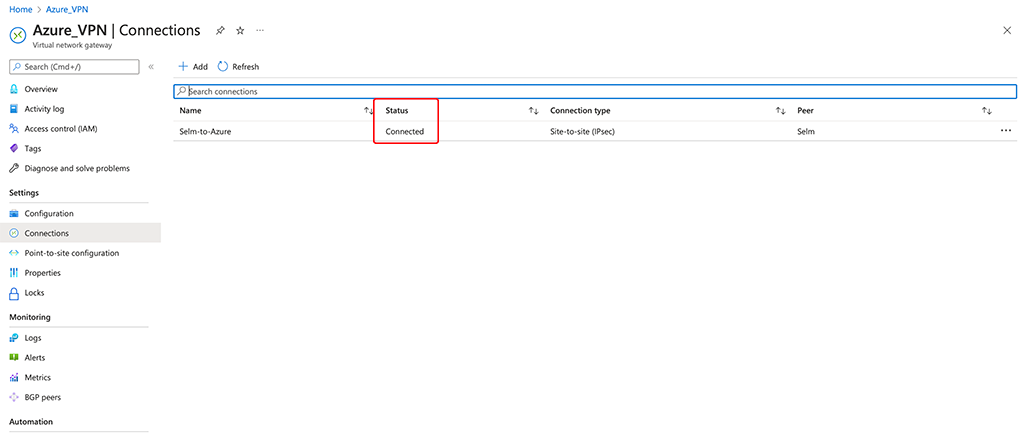
If you find this post useful, leave me a comment and share your feedback with me. You can also buy me Pizza, using the “Buy me a Pizza” button on the right, to support this blog and keep the IT gremlin happy.
If you would like to do me a favor, share this post with your friends and social media contacts. This would really help to make this blog more popular and help others to find the information above more easily using search engines.
Share on:
Thank you Florian, you are doing god’s work . I visit your blog every week looking for new content. Keep it up! <3 from Argentina.
Hi Vairo,
Thanks for the feedback. Really appreciated.
BR
Florian
Thank you Florian for this post. Just want to ask if something changes on Aruba Gateway configuration when IPsec tunnel mode is policy based not route based? We want to configure IKEv2 policy based IPsec with Mikrotik on other end. Thanks once more!
Hi Andrius,
Well, this is hard to tell as this depends on the configuration of the Mikrotik router on the other hand. I would say no, but it really depends if these two systems are compatible with each other.
BR
Florian
Thank you Florian for this post, it’s been a great help. In your site to site config I see that you chose 25 as your IKE policy. Assuming you custom made that option under the IKEV2 panel what do you have set up for that?
Hi RJ Arnold,
Shame on me, that I haven’t documented that. Please find it here:
https://www.arubanetworks.com/techdocs/central/sd-branch-ref-docs/sd-wan-with-azure-public-cloud.pdf
Page 104 is your friend 🙂
BR
Florian
Hi Florian !
Your blog is great ! Much appreciated from my side, it helped me understand then translate some Aruba content to colleagues !
I also write on this particular post because I am trying to mount a tunnel between Aruba gateway and another editor (Weblib Ucopia). The tunnel is mouting great, but I can’t make the flows to be redirected in it.. I miss something that I can’t find on your page.. Or maybe do you think that I try to make something that is not possible? I can totally share part of my config if it helps.. thanks !
Hi,
Thanks for your comment. Much appreciated.
A tunnel to a third party device should work as well. Basically, creating the tunnel to azure is a third party tunnel as well.
How do you know, that the tunnel is actually up?
To steer traffic through the tunnel the gateway need to know what destinations (IP addresses) are behind the tunnel. Did you use a static configuration like in the post above ar do you have a dynamic setup with routing protocols?
Best
Florian
Thanks for your answer, We knew that the tunnel was UP because from central and from the partner, it was showing up 😉 And we also were able to ping specific private adresses at the other side..
It appears that my colleague has solved it. It seems that we were missing some uplink config AT THE DEVICE LEVEL in WAN -> Uplink. Now the PBR is doing it’s job and we have all traffic needed redirecting in the tunnel (all traffic in my case)
So thanks for your answer ! Much appreciated.
Hi,
great to hear that it is now working for you. I’m here to help.
BR
Florian