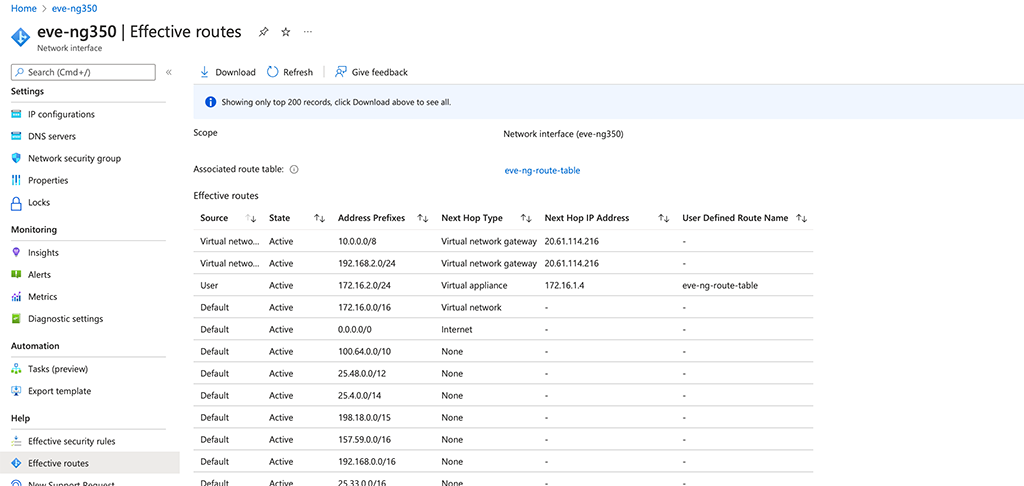
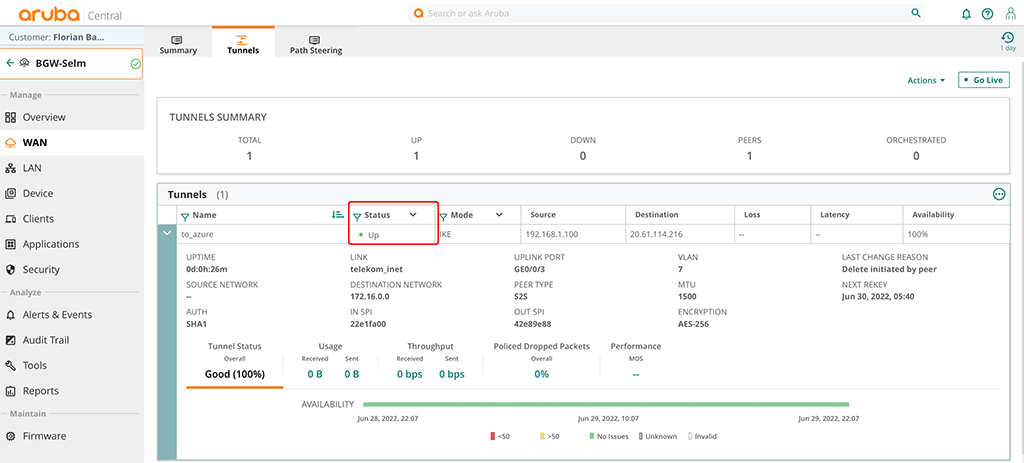
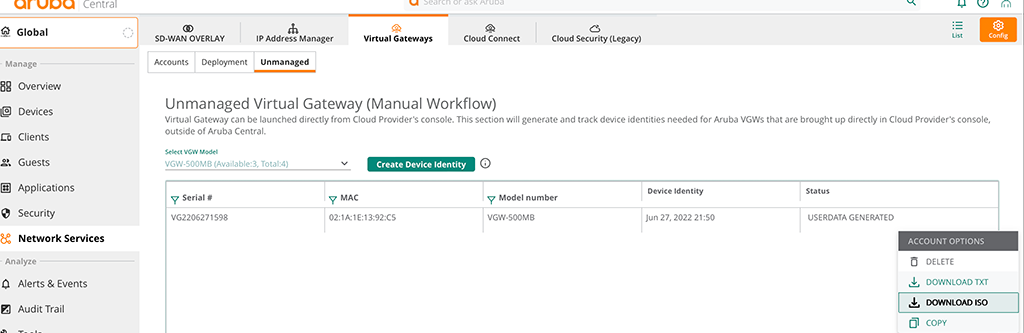
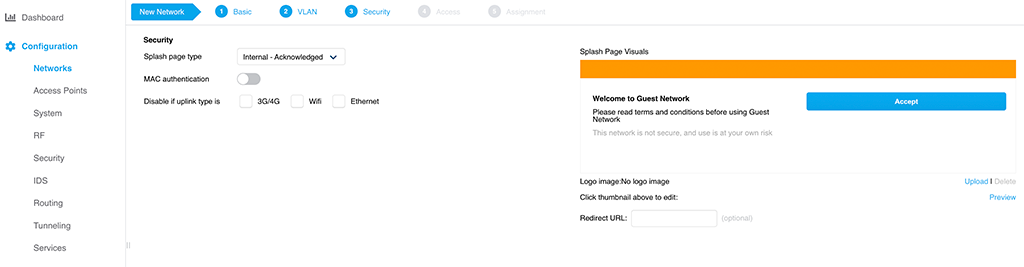
ClearPass Guest Access with Username only
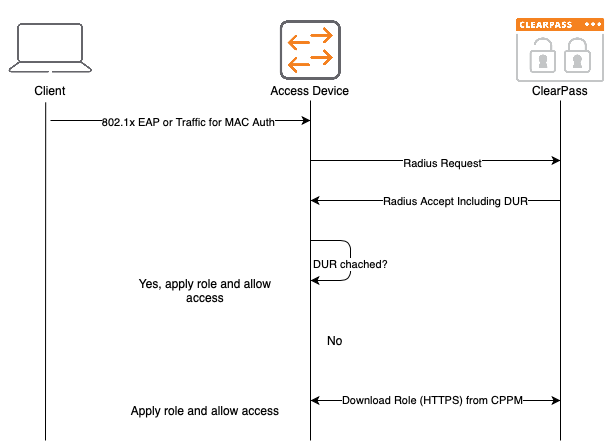
Reading Time: 17 minutesIn the past, I saw a lot of guest workflows which either did a very overloaded username and password authentication to fully authenticate the guest or the simple “Just Accept the Ts and Cs”. The first one is very complex for the guest but gives you the option to see who is online and controls … Read more