In this post I will show, how to enhance the usage of the UAM portal authentication. This will enhance the usage for mobile endpoints and for desktop/laptop users. I add this configuration to my best practices and will encourage all of my peers to use this kind of UAM portal authentication configuration.
I tested this configuration with the latest iMC UAM version, which is :
- iMC PLAT 7.1 (E0302)
- iMC UAM 7.1 (E0302)
On the Unified WLAN controller I also use one of the latest versions:
HP Comware Platform Software
Comware Software, Version 5.20.109, Release 2507P22
Copyright (c) 2010-2014 Hewlett-Packard Development Company, L.P.
LSU3WCMD0 uptime is 15 weeks, 1 day, 18 hours, 25 minutesI assume that you already configured the portal. If not, you can use this post to do the initial configuration:
How To: UAM Portal with the Unified Controller
What we gonna do, is to remove the heartbeat page, this is the one with the counter, and enable transparent authentication for mobile devices. This will make the life easier for your clients.
The Transparent authentication will detect mobile devices, like smartphones, and will bind the device mac address to the user account, after the user initially connects and authenticates on the UAM portal.
The first step is to prepare the controller to support this kind of configuration. We need to enable “mac-trigger” on the controller globally:
portal mac-trigger server ip 192.168.1.57This command will enable the “mac-trigger” globally and will use the server “192.168.1.57” for the mac authentication. Replace my IP with your iMC UAM portal IP. You also need to enable the “mac-trigger” in the VLAN interface, which is used for the UAM portal:
interface Vlan-interface52
description uam_portal
ip address 10.1.52.1 255.255.255.0
dhcp server apply ip-pool uam_portal
portal server UAM-Portal method direct
portal domain uam-portal
access-user detect type arp retransmit 5 interval 120
portal mac-trigger enable
#The command “portal mac-trigger enable” will enable the transparent authentication for this VLAN. The command “access-user detect type arp retransmit 5 interval 120” will check, if the client is still online. I choose a time period of 10min, you can adopt this to your needs. This will make sure, that clients, which are offline, get also offline within iMC UAM, as this is normally done by the heartbeat page (the one, we will disable).
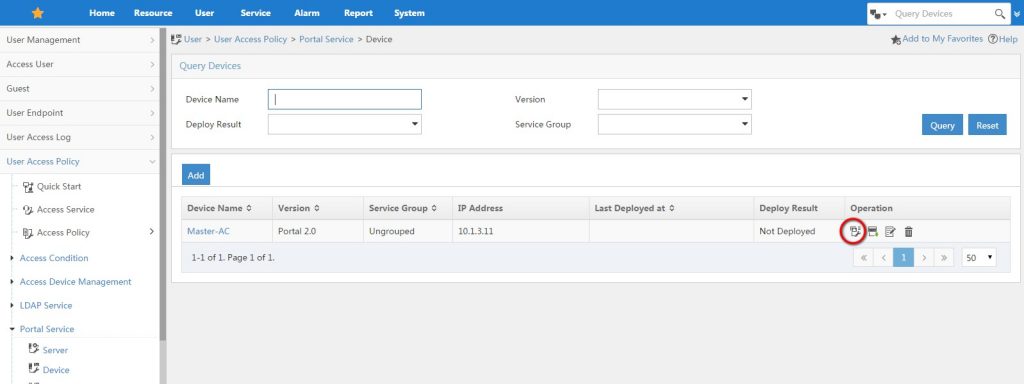
The next step, is to configure iMC UAM. Open the UAM portal authentication configuration under “User–>User Access Policy–>Portal Service–>Device” and click on the “Port Group” configuration:
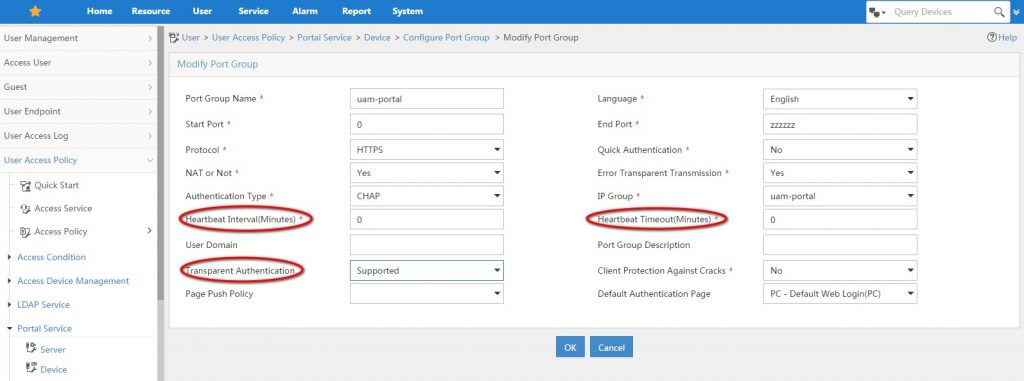
Modify the “Port Group” and set the heartbeat’s to “0” and enable “Transparent Authentication”:
To finish the configuration for transparent authentication, we also need to enable this for the access service and for the users. Go to “User–>User Access Service–>Access Service” and modify your service:
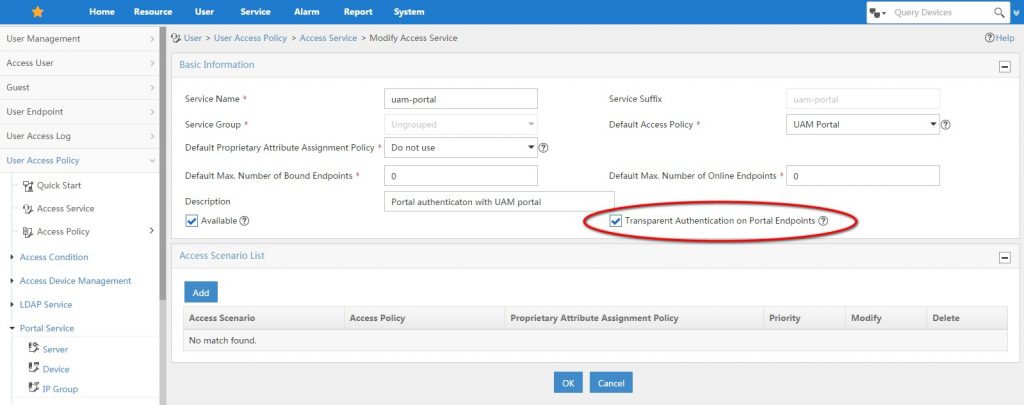
Enable the “Transparent Authentication for Portal Endpoints” and save with “OK”.
To enable the transparent authentication for access users, go to “User–>Access User–>All Access Users” and select the user you want to change. You can also select all users.
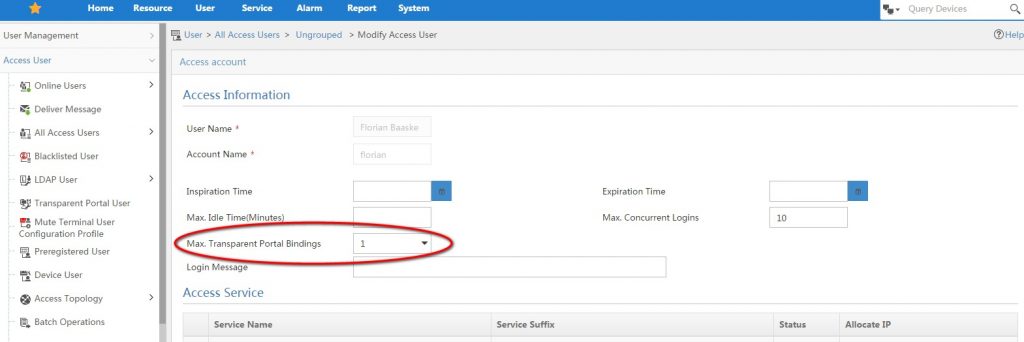
Enable “Max. Transparent Portal Bindings” by setting it to one or higher.
For guest users, you do the same, but you need to do it on the selfservice portal. Open the selfservice portal and login as a guest manager and go to “Guest Management–>All Guests” and modify the guest information:
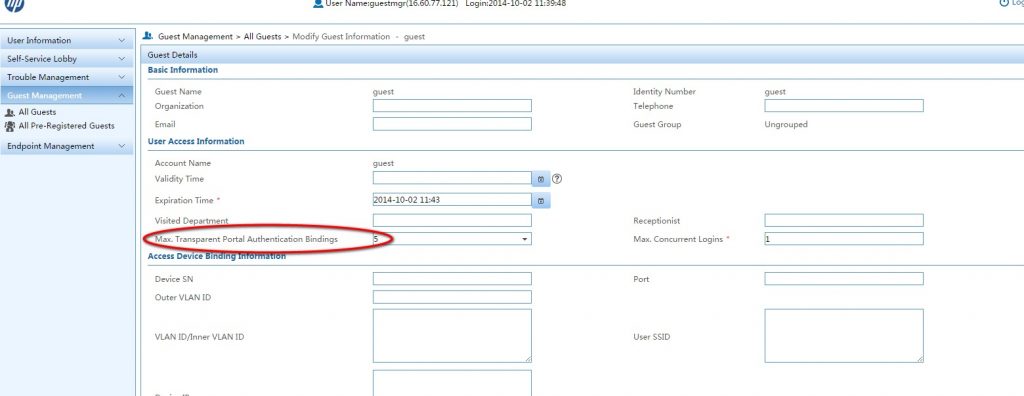
This is the same as with access user, set the “Max. Transparent Portal Bindings” to one or higher.
You should now be able to authenticate on the UAM portal page, without receiving the heartbeat page. Mobile devices should get authenticated without any user interaction, after the first successful authentication on the UAM portal.
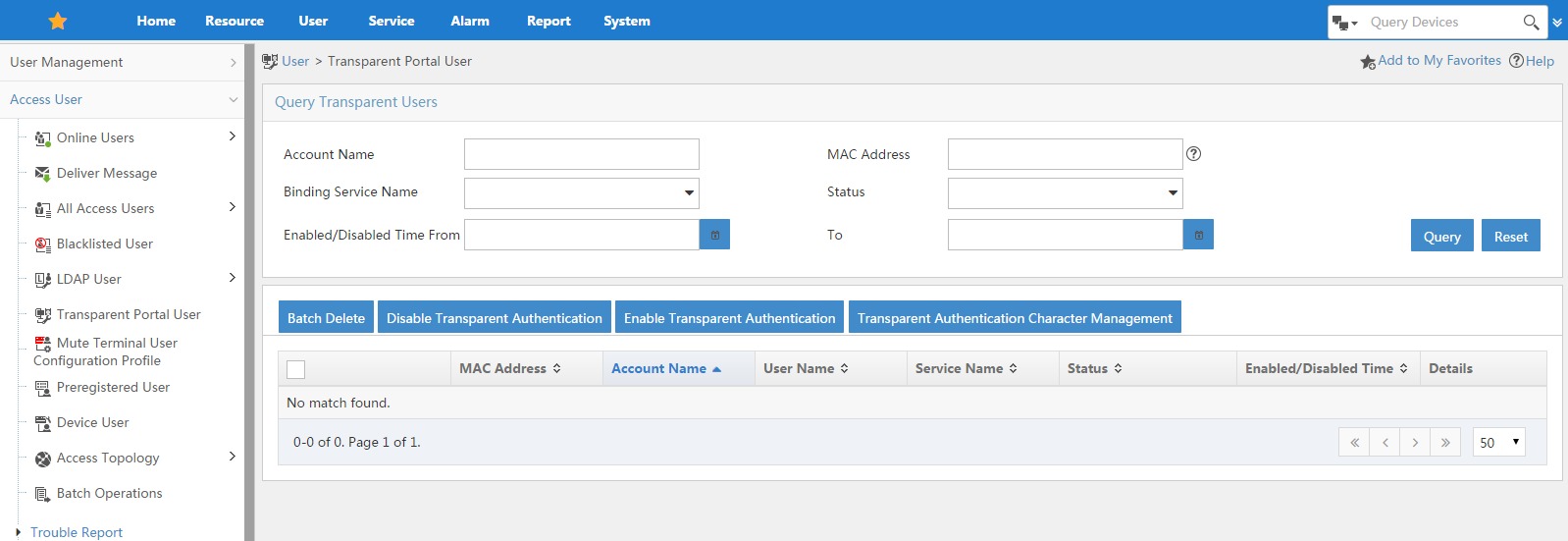
Which UAM portal users
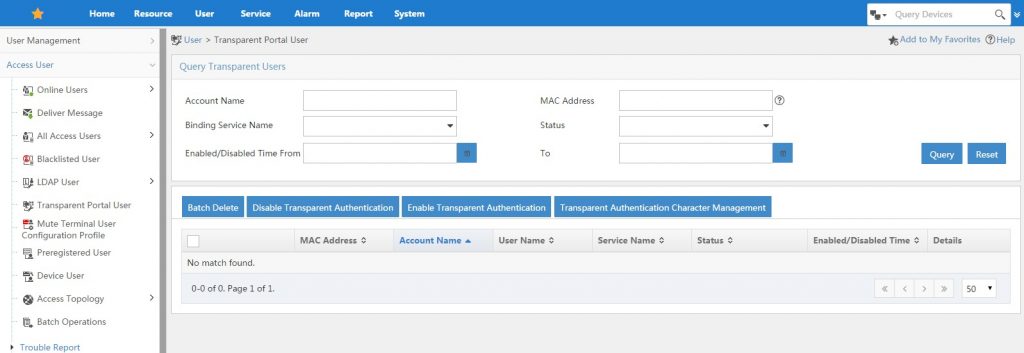
You can enable or disable this function for specific users and you can control which devices are classified as a transparent authentication device. Just click “Transparent Authentication Character Management” and have a look at the list of devices. You can also add new devices.
I’m now happy to get your feedback on this tip. Questions are very welcome as well. Just use the comment function.